Wireshark Review 2025: Still the Gold Standard for Packet Analysis?

Wireshark Review – The Global Standard for Deep Packet Inspection & Network Forensics (2025-2026)
Wireshark is the undisputed king of network protocol analyzers, providing a microscopic view of every packet traversing your network. Developed as a community-driven open-source project, it allows engineers and security specialists to “see” exactly what is happening inside their data streams. In 2025, Wireshark remains an essential tool for troubleshooting network bottlenecks, identifying malware exfiltration, and auditing encrypted traffic. With its robust support for TLS 1.3 and newly integrated Post-Quantum (PQ) algorithm dissectors, Wireshark is the “x-ray machine” of the internet, making it a non-negotiable asset for any serious cybersecurity toolkit.
VERIFIED DATA: Wireshark is maintained by the **Wireshark Foundation** and is used by over 90% of Fortune 500 network engineers. In late 2025, version 4.6 was released, featuring a 30% increase in packet processing speed and native support for ML-KEM (Kyber) and ML-DSA post-quantum cryptography dissectors, ensuring its relevance in the 2026 security landscape.
The Anatomy of a Packet: Technical Performance Metrics
Wireshark is designed for high-fidelity data capture. It operates at the Data Link Layer (Layer 2) through Application Layer (Layer 7), providing unparalleled visibility.
| Capability Metric | Wireshark 2025 Standard | Expert Technical Analysis (2025-2026) |
|---|---|---|
| Protocol Dissection | The most extensive library in existence. If a protocol exists on the internet, Wireshark can likely parse its fields. | |
| Capture Library | Npcap / Libpcap | Utilizes **Npcap** for Windows, supporting loopback capture and 802.11 monitor mode for advanced WiFi auditing. |
| Encryption Support | TLS 1.3 + PQ Cryptography | Supports decryption of modern streams when provided with **SSLKEYLOGFILE** session keys. |
| Filter Engine | Display & Capture Filters | The powerful **BPF (Berkeley Packet Filter)** syntax allows users to isolate one specific conversation out of millions of packets. |
| Extensibility | Lua Scripting | Users can write custom dissectors in **Lua** for proprietary protocols, making it indispensable for IoT and ICS security. |
Deep Dive: Mastering the Network Underworld with Wireshark
In a world where security relies on the assumption of “Zero Trust,” Wireshark is the tool used to verify that reality matches theory. While firewalls and EDRs provide high-level alerts, Wireshark provides the ground truth.
1. The “Three-Pane” View: Why It Matters
Wireshark’s interface is iconic for its three-pane structure, which hasn’t changed because it is perfectly efficient:
- Packet List Pane: A chronological list of every packet captured. In 2025, this pane includes intelligent “Coloring Rules” that instantly flag TCP errors, retransmissions, or suspicious SYN floods.
- Packet Details Pane: This is where the dissection happens. It breaks down the packet by layer (Ethernet -> IP -> TCP -> HTTP). You can see every flag, header length, and sequence number.
- Packet Bytes Pane: The raw hexadecimal and ASCII representation. This is crucial for identifying shellcode or hidden data in the payload that high-level parsers might miss.
2. Troubleshooting and Performance Optimization
Beyond security, Wireshark is the ultimate tool for network performance. By using the **Expert Information** tool, an engineer can instantly find:
- TCP Zero Window: Identifying when a server is overwhelmed and can no longer process data.
- Latency Analysis: Using the “Time Delta from Previous Packet” column to find exactly where a bottleneck is occurring in a database handshake.
- I/O Graphs: Visualizing traffic spikes in real-time to correlate them with server crashes or high-load events.
3. Modern Encryption Challenges: TLS 1.3 and Beyond
A common misconception is that Wireshark is useless in an encrypted world. This couldn’t be further from the truth. In 2025, Wireshark’s ability to handle **TLS 1.3** is its most vital feature. By configuring a browser to output session keys to a log file, Wireshark can decrypt the traffic in real-time, allowing you to see the actual JSON or HTML being sent over “secure” connections. This is essential for auditing API calls and detecting malicious C2 (Command & Control) traffic hiding in HTTPS.
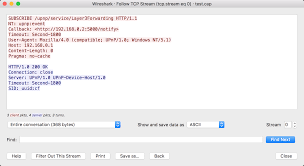
Wireshark in 2025: Using the ‘Follow TCP Stream’ feature to reconstruct a conversation and identify a security vulnerability.
Expert Security Use Cases for 2025-2026
To use Wireshark like a top-tier specialist, focus on these advanced methodologies:
Malware Traffic Analysis
When a computer is suspected of infection, Wireshark is used to look for “beacons”—regular, automated pings to unknown IP addresses. By filtering for `dns.flags.response == 0`, analysts can see which domains a system is trying to resolve, often catching DGA (Domain Generation Algorithms) used by ransomware.
VoIP Forensics
Wireshark includes a built-in **RTP Player**. It can capture SIP/RTP packets from a VoIP call, reconstruct the audio stream, and play it back. This is used by auditors to verify call quality and by investigators to intercept unauthorized communications in a controlled environment.
Comparison: Wireshark vs. The Alternatives
tcpdump / TShark
Primary Strength: Command-line based; perfect for remote servers where a GUI isn’t possible. **TShark** is actually the CLI version of Wireshark.
Charles Proxy / Fiddler
Primary Strength: Optimized specifically for HTTP/HTTPS web traffic. Much easier to use for mobile app and web development.
Burp Suite
Primary Strength: An active interception proxy designed for Penetration Testing. Unlike Wireshark, it can modify packets on the fly.
Pros & Cons: The Professional Perspective
The Pros
- Ultimate Granularity: The most detailed view of network traffic possible.
- Free & Open Source: No licensing costs; maintained by the world’s best engineers.
- Cross-Platform: Runs natively on Windows, macOS, and Linux.
- Huge Documentation: Thousands of community-created dissectors and tutorials.
The Cons
- Extreme Learning Curve: Requires a solid understanding of the OSI model and networking.
- Resource Intensive: Capturing at high speeds (10Gbps+) requires massive CPU and high-speed storage.
- “Drinking from a Firehose”: Without proper filters, the sheer volume of data can be overwhelming.
Final Verdict: The Absolute Essential for Digital Intelligence
/ 10.0
Wireshark is not just a tool; it is a fundamental skill for anyone in IT or security. In 2025, it remains the only platform that offers a completely unbiased, microscopic view of digital communication. While the learning curve is steep, the payoff is total network awareness. Whether you are debugging a broken website or hunting for state-sponsored malware, Wireshark is the definitive authority. If you aren’t using Wireshark, you are essentially flying blind in your own network.
Master Your Network Traffic Today
Don’t guess what your network is doing. Download Wireshark and see for yourself.
