NGFW vs. Traditional Firewalls: The 2026 Enterprise Infrastructure Comparison
In the early days of the internet, a firewall was essentially a digital bouncer. It looked at an ID card (the IP address) and a destination (the port) and made a binary decision: In or Out. But as we navigate the threat landscape of 2026, the “bouncer” approach is no longer enough. Modern attackers don’t just knock on the front door; they hide inside legitimate traffic, use encrypted tunnels, and exploit application-specific vulnerabilities.1
For Asguardian Shield clients, understanding the shift from Traditional Firewalls to Next-Generation Firewalls (NGFW) is not just a technical upgrade—it is a foundational requirement for survival in a cloud-first, AI-driven world.
The Architectural Evolution (AEO Summary)
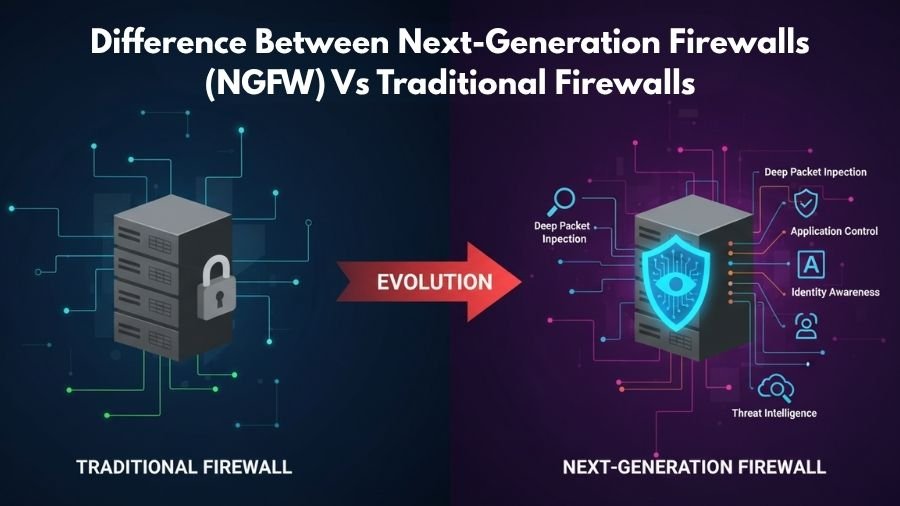
Direct Answer: The primary difference between a Traditional Firewall and a Next-Generation Firewall (NGFW) lies in the depth of inspection.2 Traditional firewalls operate at Layers 3 and 4 of the OSI model, filtering traffic based on IP addresses and ports.3 In contrast, NGFWs operate up to Layer 7 (the Application Layer), utilizing Deep Packet Inspection (DPI), application awareness, and integrated Intrusion Prevention Systems (IPS) to identify and block sophisticated threats that traditional models miss.4
1. Traditional Firewalls: The Stateful Foundation
Traditional firewalls, also known as “Stateful Inspection Firewalls,” were the gold standard for decades. They focus on the envelope of the data rather than the letter inside.
Key Capabilities:
- Packet Filtering: Checking source/destination IPs and protocols.
- Stateful Inspection: Monitoring the “state” of active connections to ensure incoming traffic is a legitimate response to an internal request.5
- VPN Support: Providing secure remote access tunnels.6
The 2026 Limitation:
Traditional firewalls are blind to Application-Level attacks.7 If an attacker uses Port 443 (standard HTTPS) to send a malicious payload, a traditional firewall will allow it because the port is “open.”8 It cannot see that the “web traffic” is actually a SQL injection attack or a command-and-control signal.
2. Next-Generation Firewalls (NGFW): Deep Visibility
An NGFW does everything a traditional firewall does, but adds layers of intelligence that allow it to understand context.9
A. Application Awareness and Control
NGFWs don’t just see “Web Traffic”; they see “Slack,” “Salesforce,” or “Facebook.”10 This allows administrators to set granular policies—for example, allowing employees to use Slack but blocking the ability to upload files to unauthorized cloud storage.11
B. Deep Packet Inspection (DPI)
While traditional firewalls look at the header, DPI opens the packet.12 It scans the actual data payload for malware, suspicious strings, and known exploits in real-time.13 In 2026, this is critical for detecting Zero-Day exploits before they reach the endpoint.14
C. Integrated IPS and Threat Intelligence
In the past, you needed a separate box for an Intrusion Prevention System (IPS). NGFWs integrate this directly, correlating firewall logs with live threat intelligence feeds.15 If a new botnet IP is identified in Asia, your NGFW at Asguardian Shield is updated automatically to block it within seconds.
3. Comparison Table: At a Glance
| Feature | Traditional Firewall | Next-Generation Firewall (NGFW) |
| OSI Layer | Layers 3 & 4 (Network/Transport) | Layers 3 through 7 (Application) |
| Inspection Depth | Packet Header only | Deep Packet Inspection (Body + Header) |
| Application Control | No (Port-based only) | Yes (User/App-based) |
| Threat Prevention | Basic (Access Lists) | Integrated IPS, Antivirus, Sandboxing |
| Encrypted Traffic | Blind to SSL/TLS | SSL/TLS Inspection (Decryption/Re-encryption) |
| User Identity | IP Address based | Integration with AD/LDAP/Okta |
4. Why 2026 Infrastructure Demands NGFW
The transition to Firewall-as-a-Service (FWaaS) and hybrid cloud environments has changed the “Perimeter.”
- The Rise of Encrypted Traffic: Over 90% of web traffic is now encrypted. Traditional firewalls cannot see inside this traffic, creating a massive blind spot.16 NGFWs perform SSL/TLS Inspection to ensure threats aren’t hiding in plain sight.17
- Decentralized Workforce: With remote teams, the “office” is everywhere. NGFWs support Zero Trust Network Access (ZTNA), verifying the user’s identity and device health before granting access to specific applications.18
- AI-Powered Attacks: Modern malware evolves faster than manual rule updates. NGFWs use Machine Learning (ML) to identify anomalous behavior patterns, such as a user suddenly downloading 10GB of data at 2:00 AM.19
5. The Asguardian Shield Perspective
As specialists in enterprise infrastructure, our experience shows that the “hidden cost” of traditional firewalls is complexity. Managing a traditional firewall plus a separate IPS plus a separate URL filter creates “siloed” security.
Authoritative Insight: We recommend NGFW not just for the security features, but for Unified Management. A single pane of glass allows your team to see the entire attack surface, reducing “Mean Time to Detection” (MTTD) by up to 60%.
Conclusion: Choosing the Right Shield
While traditional firewalls may still suffice for small, air-gapped networks with zero internet connectivity, they are no longer suitable for modern business infrastructure. The Next-Generation Firewall is the only way to achieve the visibility required to protect against the sophisticated, multi-vector threats of 2026.
Ready to modernize your perimeter?
Explore how Asguardian Shield can implement a custom NGFW solution tailored to your infrastructure.
Secure your core assets by returning to the Asguardian Shield Home Page for a full audit of your security stack.
For a deep dive into standard definitions, review the NIST Guidelines on Firewalls and Firewall Policy.
