Prowler Review 2025: Is It Still the Best Open-Source CSPM for AWS?

Prowler Review – The Definitive Open-Source Authority for Multi-Cloud Security Posture & Compliance (2025-2026)
Prowler is the world’s most widely adopted open-source tool for cloud security assessments, moving far beyond its origins as a simple AWS auditing script into a comprehensive multi-cloud powerhouse. It is designed to perform deep-dive security audits, continuous monitoring, and automated hardening against CIS Benchmarks, GDPR, and SOC2. In 2025, with the launch of Prowler v4 and v5, the tool has integrated Lighthouse AI to provide autonomous risk reasoning and Attack Path Visualization. Whether you are a solo DevSecOps engineer or managing an enterprise-scale multi-cloud environment, Prowler provides the granular, agentless visibility required to “Secure ANY cloud at AI speed” without the massive licensing costs of proprietary CSPM tools.
VERIFIED DATA: Prowler is an AWS-recognized partner and is used by over 45 million cloud workloads globally. In 2025, Prowler released **v4.0**, migrating to a unified multi-provider architecture and introducing **OCSF v1.1.0** output support. Its community is among the most active in cybersecurity, with over 12,000 GitHub stars and 300+ contributors worldwide, ensuring rapid updates for the latest AWS services and 2026 compliance mandates.
Cloud Posture Intelligence: 2025 Technical Metrics
Prowler’s architecture is agentless, utilizing cloud-native APIs (Boto3 for AWS, Azure SDK) to perform non-intrusive metadata analysis of your entire infrastructure.
| Monitoring Metric | Prowler 2025 Standard | Expert Technical Analysis (2025-2026) |
|---|---|---|
| Scan Velocity | Scan speed has been optimized in v4.x through parallel execution, allowing a full 300-check audit of a standard AWS account in record time. | |
| Compliance Coverage | 30+ Frameworks | Supports CIS 4.0, GDPR, HIPAA, NIST CSF 2.0, and ISO 27001. New 2025 support includes **C5 (Azure/GCP)**. |
| Remediation (Fixer) | Automated “Prowler Fixer” | The new `–fix` flag allows for programmatic remediation of misconfigurations (e.g., closing open S3 buckets) directly from the CLI. |
| Output Schema | OCSF v1.1.0 / JSON / CSV | Normalized output across all providers (AWS/Azure/GCP) makes it ready for ingestion into any modern SIEM or Data Lake. |
| Visual Context | Attack Path Visualization | New for late 2025, Prowler maps how an attacker could move laterally between services, identifying “Blast Radius” risks. |
Deep Dive: The Shift to “Open Cloud Security” with Prowler v4
In the 2025 digital era, “Security by Obscurity” is dead. Prowler has led the movement toward Open Cloud Security, proving that transparent, community-vetted code is the only way to keep pace with the hyper-velocity of cloud service releases.
1. Multi-Cloud & Kubernetes Architecture
While Prowler was born in AWS, the 2025 release has fully matured its Multi-Cloud capabilities.
- Unified Provider Engine: Prowler v4 uses a common provider structure. You can run `prowler aws`, `prowler azure`, or `prowler gcp` with the exact same CLI experience and output format.
- Kubernetes Support: The new Kubernetes provider audits your clusters against **CIS Benchmark 1.8**, checking for RBAC misconfigurations, insecure API server settings, and vulnerable etcd configurations.
- Infrastructure as Code (IaC): Late 2025 updates introduced a native IaC provider, allowing you to scan Terraform and CloudFormation templates for security gaps *before* they are deployed.
2. Lighthouse AI: Autonomous Cloud Defense
The most revolutionary addition in 2025 is Lighthouse AI, Prowler’s autonomous security assistant.
- Reasoning over Graphs: Lighthouse AI doesn’t just look at alerts; it reasons over Prowler’s internal **Knowledge Graph**. It can answer questions like, “Which S3 buckets are accessible by this specific IAM role that also has cross-account trust?”
- Prioritized Risk Scoring: It replaces static “High/Medium/Low” labels with the Prowler ThreatScore, which calculates the real-world attackability of a resource based on its connectivity and permissions.
- Natural Language Remediation: You can ask Lighthouse AI to generate the exact CLI command or Terraform block needed to fix a specific compliance failure, drastically reducing Mean Time to Remediation (MTTR).
3. Attack Path Visualization: Seeing the “Blast Radius”
Cloud misconfigurations are rarely isolated. An exposed EC2 instance is dangerous, but an exposed EC2 instance with an IAM role that can access an S3 bucket containing PII is a catastrophe.
Prowler’s 2025 **Attack Path Visualization** turns fragmented findings into a connected risk map. It identifies the “earliest point of compromise” and shows the precisely linked route an attacker would take to escalate privileges or reach sensitive data. This feature, available in **Prowler Cloud**, allows teams to focus their limited resources on the specific nodes that break the entire attack chain.
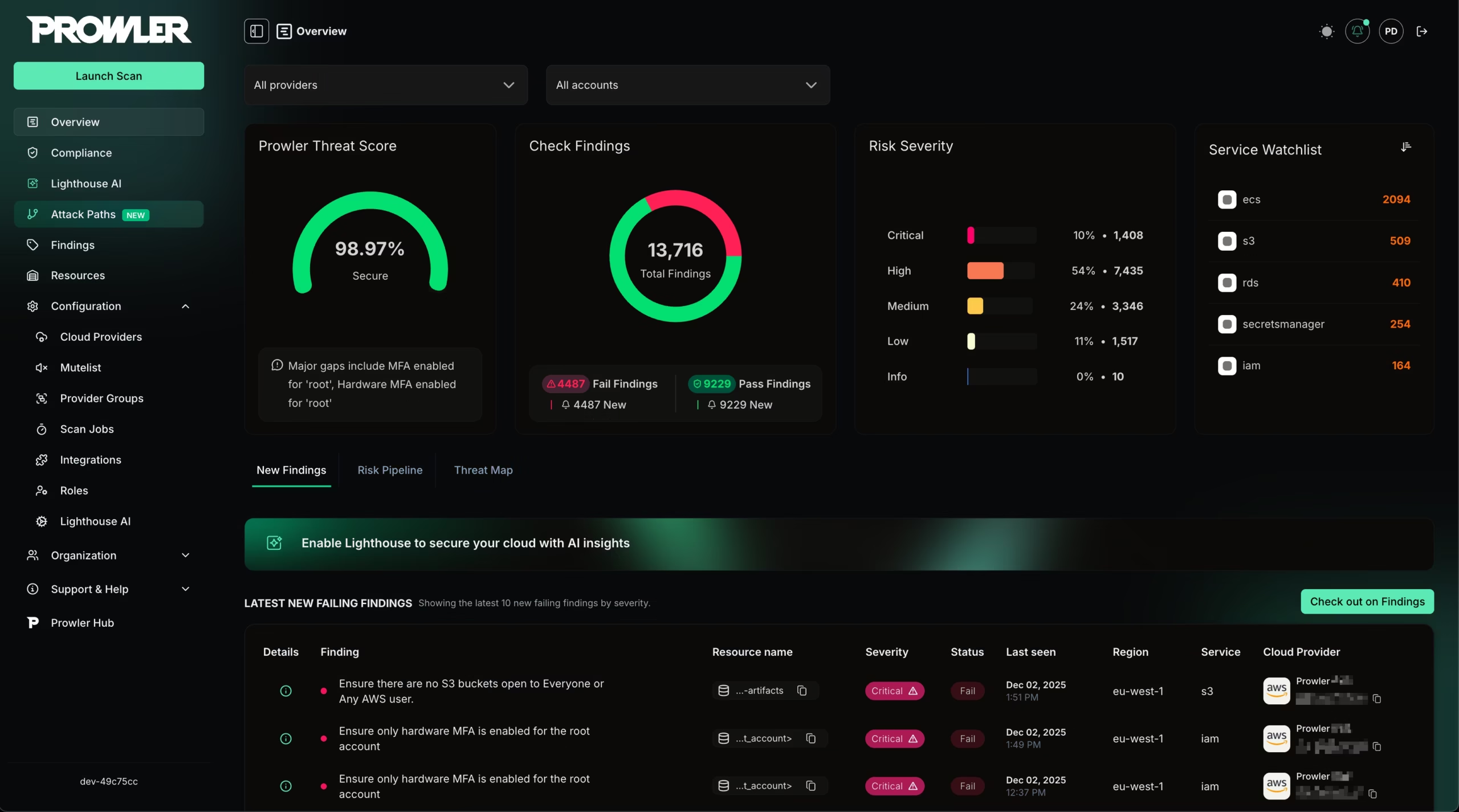
The Prowler Cloud Dashboard (2025): Transforming millions of raw audit logs into clear, actionable risk paths across multiple AWS and Azure accounts.
Expert Setup & Implementation for 2026 Compliance
To deploy Prowler at an enterprise level in 2025-2026, you must integrate it into your DevSecOps Pipeline rather than running it as a manual audit.
- Run as a Periodic Lambda/Container: Deploy Prowler as an AWS Fargate task or a Lambda function that triggers every 24 hours to detect “Configuration Drift.”
- Enable Security Hub Integration: Use the `–security-hub` flag to push Prowler findings directly into AWS Security Hub. This centralizes Prowler data with other native AWS security signals for a single-pane-of-glass view.
- Custom Frameworks for GDPR/HIPAA: Don’t run every check every time. Use the `–framework gdpr` or `–framework hipaa` flags to run only the specific controls required for your regulatory audits.
- Muting False Positives Programmatically: In v4, use the Mute List feature to permanently silence alerts for resources that are “Secure by Design” or have documented business exceptions, keeping your signal-to-noise ratio high.
- Automated Fixing with `–fix`: For low-risk, high-impact misconfigurations (like enabling S3 Public Access Block), use the new fixer module to enforce security baselines automatically.
Who is Prowler Best Suited For?
- DevSecOps Teams: Seeking a lightweight, CLI-first tool that can be embedded into CI/CD pipelines and automated workflows.
- Compliance & Audit Officers: Requiring “Audit-Ready” reports for CIS, GDPR, and PCI-DSS with zero manual effort.
- Cloud Security Architects: Managing multi-cloud (AWS/Azure/GCP) environments who need a unified security baseline across all providers.
- Incident Responders: Utilizing Prowler’s “Forensics Readiness” checks to ensure that logging and monitoring are correctly configured before an event occurs.
Comparison: Prowler vs. AWS Config vs. Wiz
AWS Config
Primary Strength: Continuous resource tracking and configuration history. Weakness: Limited to AWS only; can be significantly more expensive due to “Per-Rule” pricing compared to Prowler’s scan-based model.
Wiz / Orca
Primary Strength: The “Cadillac” of CNAPPs. Offers deep workload protection and vulnerability scanning. Weakness: Extremely high cost (typically $50k+ entry) making it inaccessible for smaller teams or high-velocity startups.
Steampipe
Primary Strength: SQL-based cloud querying. Excellent for custom reporting. Weakness: Not specifically a security scanner; requires the user to write the security logic themselves.
Pros & Cons: The Professional Perspective
The Pros
- 100% Transparent: Every security check is open for review on GitHub—no “black box” logic.
- Zero Lock-in: Avoid the proprietary data formats of commercial CSPM vendors.
- AI-Powered Remediation: Lighthouse AI makes fixing cloud risks faster than ever.
- Extremely Scalable: Scan one account or a 5,000-account AWS Organization with ease.
The Cons
- CLI Management: While powerful, managing thousands of CLI results across many accounts can become “alert fatigue” without the **Prowler Cloud** dashboard.
- Azure/GCP Depth: While rapidly improving in 2025, Prowler’s check library for AWS is still deeper than its libraries for Azure and GCP.
- Manual Deployment: The open-source version requires you to manage your own compute (Lambda/Fargate) and storage for the results.
Final Verdict: The Gold Standard for Modern Cloud Governance
/ 10.0
Prowler is the rare tool that manages to be both “Enterprise-Ready” and “Developer-Friendly.” In 2025, it has successfully transitioned from a collection of shell scripts into a full-spectrum Cloud Security platform. By combining the transparency of open-source with the cutting-edge intelligence of Lighthouse AI, Prowler has disrupted the CSPM market, providing a level of security that was previously locked behind six-figure enterprise contracts. If you are serious about cloud security in 2026—whether for a single S3 bucket or a global multi-cloud empire—Prowler is the most important, cost-effective, and powerful tool in your security stack.
Secure Your Cloud at AI Speed
Don’t wait for a misconfiguration to become a breach. Use the tool trusted by over 45 million workloads.
