Tor Browser Review 2025: The Ultimate Tool for Anonymity & Onion Access

Tor Browser Review – The Ultimate Fortress for Anonymity and Censorship Resistance (2025)
Tor Browser (The Onion Router) is the world’s most powerful tool for digital anonymity, designed to protect users against state-level surveillance and corporate tracking. By routing your connection through a decentralized network of three volunteer-run relays, it ensures that no single entity can link your identity to your activity. In 2025, Tor remains the exclusive gateway to .onion hidden services, providing end-to-end encryption that bypasses even the most restrictive national firewalls.
VERIFIED DATA: Tor Browser is developed by The Tor Project, a 501(c)(3) nonprofit. In late 2025, the browser was updated to Version 15.0, integrating Vanguards-lite to mitigate guard discovery attacks. It remains the only browser that natively strips metadata and canvas fingerprinting to make all users appear identical to trackers.
Anonymity Metrics: The Onion Routing Analysis
Tor does not operate like a standard proxy. It utilizes Telescoping Circuit Building, where each node in the path only knows the identity of the node immediately before and after it.
| Security Metric | Tor Project Rating | Expert Technical Analysis |
|---|---|---|
| Encryption Protocol | Traffic is encrypted for the Exit, Middle, and Guard nodes. Each relay peels off one layer, ensuring the source IP and destination are never visible to the same server. | |
| Anti-Fingerprinting | Industry Leader (10/10) | Utilizes Letterboxing to standardize window sizes and blocks Canvas/Audio Fingerprinting. This makes your browser profile indistinguishable from millions of other Tor users. |
| Censorship Bypass | Bridges & Snowflake | If the Tor network is blocked by your ISP, Pluggable Transports (obfs4, Snowflake) disguise Tor traffic as regular web traffic or video calls to bypass Deep Packet Inspection (DPI). |
| Privacy Baseline | Zero-Persistence | By default, Tor Browser operates in Permanent Private Browsing Mode. History, cookies, and cache are purged instantly upon closing the application. |
| Hidden Service Access | Native .Onion Support | Enables access to Version 3 Onion Services, which provide 56-character addresses and end-to-end encryption without the need for a Central Certificate Authority. |
Tor Architecture: Technical Pillars of Privacy
The Tor Browser is a heavily modified version of Firefox ESR, stripped of all telemetry and hardened with proprietary security extensions.
1. The Three-Hop Circuit Logic
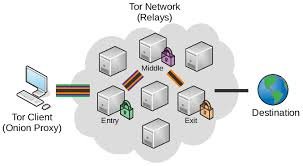
The core of onion routing lies in the separation of identifying data from the traffic destination.
- Entry Guard: The only node that knows your real IP address. Tor sticks with a few reliable guards to prevent Sybil attacks.
- Middle Relay: An intermediary that obscures the connection between the Guard and the Exit node. It sees only encrypted data passing through.
- Exit Node: The final hop that decrypts the last layer and sends the request to the destination website. It knows the destination but never your identity.
2. Pluggable Transports & Bridges
For users in restrictive regimes (like China, Iran, or Russia), Tor offers specialized “Bridges” to maintain access.
- obfs4: Makes Tor traffic look like unidentifiable “random” data to prevent automated blocking.
- Snowflake: Routes your traffic through temporary proxies run by volunteers in their browsers, making it nearly impossible for censors to block all entry points.
- Meek (Azure/Cloud): Uses “domain fronting” to make Tor traffic appear as if it is connecting to a major cloud provider.
3. Integrated Security Extensions
Tor comes pre-configured with the most aggressive security tools available.
- NoScript: Allows users to disable JavaScript globally or per-site, stopping scripts from executing and revealing your system’s true location.
- HTTPS-Only Mode: Automatically upgrades all connections to encrypted HTTPS, protecting against Exit Node eavesdropping on unencrypted sites.
- Circuit Display: Allows you to view the exact path your data is taking through the world and “New Identity” to instantly rebuild the circuit.
The Tor Browser Circuit Display shows the three-node path through different countries, ensuring your IP address is never revealed to the destination.
2025 Performance Evaluation: Speed vs. Anonymity
Anonymity has a performance cost. Because traffic is routed through three global points, latency is higher than a standard browser or VPN.
Operational Analysis (2025)
- Network Speed: While slower than fiber, the Tor network has seen 30% bandwidth growth in 2025, making 1080p video streaming possible on high-capacity circuits.
- Connection Stability: Circuits are refreshed every 10 minutes or upon closing the app, providing Perfect Forward Secrecy.
- Platform Support: Available natively on Windows, macOS, Linux, and Android. (iOS users should use the Onion Browser as the official alternative).
- Search Integration: Features DuckDuckGo as the default search engine, which has a dedicated .onion link for even higher privacy.
Tor is not intended for high-bandwidth activities like gaming or 4K torrenting. It is a specialized tool for communication, research, and sensitive browsing.
Critical Safety Recommendations & OpSec
Even the best tool can fail due to human error. Follow these rules for maximum 2025 safety:
- Set Security Level to “Safest”: This disables JavaScript globally, protecting you from the majority of deanonymization exploits.
- Don’t Resize the Window: Keep the browser at its default size. Resizing allows sites to determine your screen resolution, aiding in fingerprinting.
- Never Use a VPN with Tor (unless necessary): For most, “Tor over VPN” adds an unnecessary point of failure. Only use a VPN if you must hide Tor usage from your ISP.
- Avoid Personal Accounts: Logging into Facebook, Gmail, or Twitter via Tor links your identity to that specific Tor circuit.
- Open Downloads Offline: If you download a PDF or DOC, disconnect your internet before opening it to prevent “phone-home” beacons from revealing your real IP.
Who is Tor Browser Best Suited For?
- Journalists & Whistleblowers: Individuals needing to communicate and share documents without fear of interception.
- Users in Censored Regions: People in countries that block access to social media, news, or human rights websites.
- Privacy Advocates: Anyone who wants to browse the web without being profiled by big tech or ISP tracking.
- Hidden Service Researchers: Users needing to access .onion forums and markets securely.
Who Should Consider an Alternative?
- Daily Casual Streamers: If you just want to watch Netflix abroad, a Premium VPN (ExpressVPN/NordVPN) is much faster and more reliable.
- Gamers: High latency (ping) makes Tor unusable for online gaming.
- Sensitive Financial Users: Many banks will auto-block connections coming from Tor Exit Nodes as a fraud prevention measure.
Top Anonymity Alternatives
Mullvad Browser
Primary Strength: Developed with the Tor Project, it offers **Tor-level Fingerprinting Protection** but works over a standard VPN for better speed.
I2P (Invisible Internet Project)
Primary Strength: A **Decentralized Network** focusing on internal “garlic routing.” It is better for peer-to-peer file sharing and internal hidden services.
Tails OS
Primary Strength: The ultimate step up. A **Live Operating System** that routes all system traffic through Tor and leaves zero trace on the hardware.
Final Verdict: The Definitve Tool for Digital Freedom
/ 10.0
Tor Browser remains the undisputed king of online anonymity. In an era of rampant data collection and AI-driven surveillance, it provides a mathematically-backed shield for your identity. While it requires a trade-off in speed, the Peace of Mind and access to the unrestricted internet it provides is unparalleled. For anyone serious about privacy or living under censorship, Tor is not just a tool—it is a digital necessity in 2025.
Expert Security Conclusion
When used correctly with high Operational Security (OpSec), Tor Browser is the most secure way to navigate the modern internet without leaving a trace.
Reclaim Your Right to Privacy
Download the world’s most trusted tool for anonymous browsing and censorship resistance.
