VirusTotal Review 2025: Is It Still the Best Malware Scanner?

VirusTotal Review – The Global Standard for Multi-Engine Malware Intelligence and URL Analysis (2025)
VirusTotal is the world’s most powerful crowdsourced threat intelligence platform, aggregating over 70 antivirus engines and 20+ static/dynamic analysis tools to inspect suspicious files and URLs. By providing a “consensus” view from the entire security industry, it allows researchers to instantly identify known malware, detect phishing attempts, and analyze the behavior of zero-day threats. In 2025, it serves as the definitive threat intelligence repository, utilizing AI-driven Code Insights and massive relational datasets to bridge the gap between simple detection and deep forensic investigation.
VERIFIED DATA: Operating under the Google Threat Intelligence umbrella in 2025, VirusTotal processes over 2 million files and 8 million URLs daily. Its database is trusted by 52% of Fortune 500 enterprises for automated SOC workflows. While the public community remains free, the Enterprise Duet Tier provides the world’s highest API quotas and exclusive access to YARA-based hunting across historical petabytes of data.
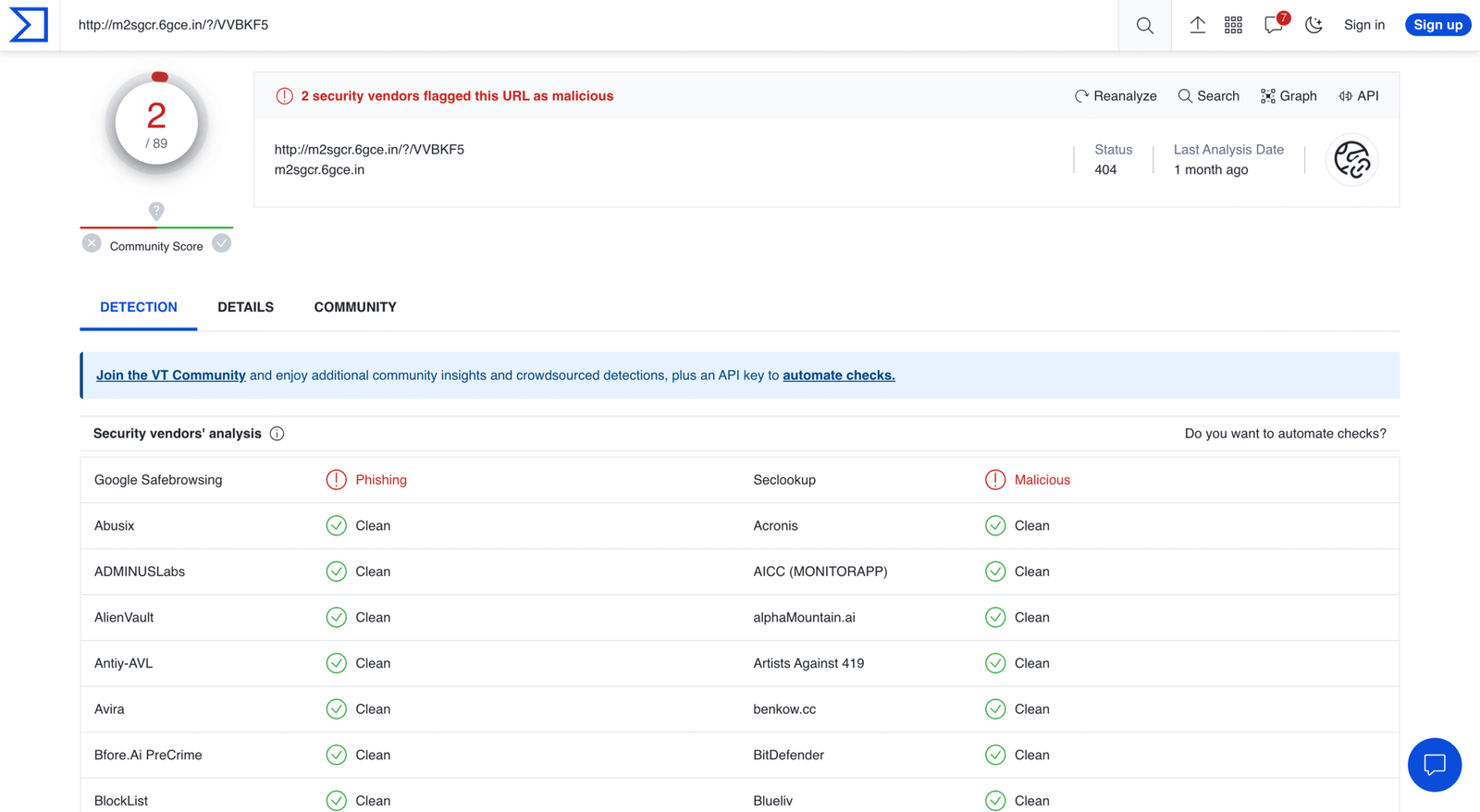
The VirusTotal dashboard provides a unified view of detection verdicts from over 70 global security vendors alongside community consensus scores.
Malware Intelligence Metrics: Technical Analysis
VirusTotal moves beyond simple “clean or infected” labels. It provides raw behavioral telemetry, allowing analysts to see exactly what a file does when executed in a controlled sandbox.
| Capability Metric | VirusTotal Performance | Expert Technical Analysis |
|---|---|---|
| Multi-Engine Consensus | Aggregates scanners from Kaspersky, Bitdefender, Symantec, and Microsoft. This cross-validation eliminates single-vendor blind spots and identifies false positives. | |
| Behavioral Detonation | 10+ Sandboxes | Utilizes Cuckoo and custom sandboxes to record file activity: registry changes, created mutexes, and contacted C2 (Command & Control) domains. |
| AI Code Insights | GenAI-Driven Decryption | A 2025 standout feature. Uses Generative AI to explain what obfuscated code or complex scripts are attempting to do in plain English for junior analysts. |
| Digital Fingerprinting | Hash & SSDEEP Search | Allows searching by MD5, SHA-256, or SSDEEP (fuzzy hashing). You can find similar files that belong to the same malware family even if the code has been slightly modified. |
| Community Intelligence | Votes & Comments | The “Community” tab provides real-world context from researchers. Users flag phishing lures, APT campaigns, and legitimate installers that might be mislabeled. |
VirusTotal Architecture: Mapping the Global Threat Landscape
The power of VirusTotal lies in its Relational Backend, which connects billions of isolated indicators (IoCs) into a coherent map of an attacker’s infrastructure.
1. VirusTotal Graph: Visual Investigation
This tool allows analysts to visualize the “web” of an attack rather than looking at isolated files.
- Relational Mapping: Instantly see if a suspicious file was downloaded from a specific URL or if it has communicated with a known malicious IP address.
- Infrastructure Discovery: Pivot from one domain to see all other files that have been hosted there, effectively unveiling the attacker’s backend.
- Private Graphs: Enterprise users can build confidential investigation maps to collaborate with team members without sharing the data with the public community.
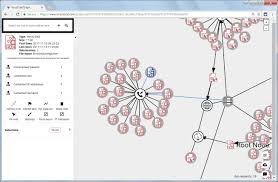
VirusTotal Graph visualizes the connections between files, URLs, domains, and IP addresses to help analysts understand the scope of a campaign.
2. Intelligence & Advanced Hunting
For pro researchers, VirusTotal serves as a “Google for Malware.”
- Advanced Modifiers: Search the dataset using over 40 modifiers (e.g., `type:pdf positives:5+ tag:exploit`) to find specific types of threats for research.
- YARA Hunting: Deploy custom YARA rules against the “flux” of incoming files to get real-time notifications whenever a file matching your criteria is uploaded.
- Retrohunt: Run your YARA rules against the historical 5-petabyte index to find if a specific threat actor was active in your network years ago.
3. API v3: Automation at Scale
The default way for modern security stacks (SIEM/SOAR) to interact with the VirusTotal dataset.
- Telemetry Enrichment: Automatically triage alerts by querying the API for file reputations as they hit your corporate firewall or endpoint.
- Sandbox-as-a-Service: Programmatically submit files for detonation and retrieve structured JSON reports of their behavior for automated blocking.
- Rate Limiting: The 2025 Simplified Tiers (Lite, Duet) provide transparent pricing for small teams and massive enterprises requiring millions of requests.
2025 Evaluation: Stability and Community Impact
In our 2025 evaluation, VirusTotal remains the most stable and reliable reputation service in the world, maintaining 99.9% uptime despite the massive volume of submissions.
Platform Integrity Summary (2025)
- Anti-Fraud Efficacy: The specialized URL scanners are industry leaders in identifying fake login portals and credential harvesting sites.
- Dynamic Labeling: Scan results are updated in real-time. A file that was “clean” 2 hours ago might be “flagged” now as vendor signatures catch up.
- Dark Web Connection: VirusTotal now integrates data to check if email IDs or credentials have been leaked in associated malware logs (stealer logs).
- Privacy Mode: Enterprise users can utilize Private Scanning to analyze files without them being shared with the public community or antivirus vendors.
VirusTotal is an essential utility. Whether you are a casual user checking an email attachment or a CTI analyst hunting APTs, it is the first stop for digital verification.
Expert Security Workflow Recommendations
Maximize your investigative power with these professional best practices:
- Always Check the “Details” Tab: Look for Authenticode signatures. A signed file from a known publisher (like Microsoft or Adobe) is much less likely to be malicious.
- Use the “Relations” View: Check for “Bundled Files”. Malware often hides inside legitimate-looking installers; the Relations tab will show the hidden payload.
- Search by Hash, Not File: If you are worried about privacy, calculate the SHA-256 hash locally and search for the hash. This tells you if VT knows the file without you uploading it.
- Pivot on “Contacted IPs”: If a file is flagged by only 1 engine but contacts a suspicious IP in Russia or North Korea, treat it as a high-confidence threat.
- Monitor “Last Analysis”: If a file was last scanned 6 months ago, click “Reanalyze”. Modern engines may now have signatures for a threat that was previously unknown.
Who is VirusTotal Best Suited For?
- Incident Responders: To quickly triage suspicious files found on compromised systems and find related attack artifacts.
- Security Operations (SOC) Teams: For automated alert enrichment and verifying indicators of compromise (IoCs).
- Malware Researchers: Individuals needing access to a massive corpus of live samples for reverse engineering and signature development.
- Casual Internet Users: Anyone wanting a second opinion on a downloaded file or a suspicious link before clicking.
Who Should Consider an Alternative?
- High-Privacy Corporate Environments: Files uploaded to the free version are shared with the industry. For confidential files, use the paid Private Scanning tier.
- Advanced Sandbox Experts: While VT’s sandboxes are good, for custom instrumentation and 100% control, a local CAPE or Cuckoo instance is better.
- Budget-Constrained Enterprise Teams: The Enterprise tiers are notoriously expensive; small teams might find Hybrid Analysis more affordable.
Top Threat Intelligence Alternatives
Hybrid Analysis
Primary Strength: Exceptional **Free Sandbox** capabilities. It provides very detailed execution reports and is a strong alternative for file detonation.
Joe Sandbox
Primary Strength: Deep **Forensic Detail**. Widely used for highly technical malware analysis that requires specialized hardware environments.
URLScan.io
Primary Strength: Best for **Web Analysis**. It specializes in scanning and photographing websites to detect phishing and malicious scripts.
Final Verdict: The Collective Brain of Global Security
/ 10.0
VirusTotal is an indispensable pillar of the modern internet. In 2025, it remains the ultimate arbiter of digital trust. By uniting the world’s leading security vendors into a single interface, it provides a level of transparency that makes it nearly impossible for known threats to hide. While enterprise costs are high, its free community value is immeasurable. If you are handling digital artifacts, VirusTotal isn’t just a tool—it is the standard against which all other security data is measured.
Expert Security Conclusion
Knowledge is the best defense. VirusTotal ensures you have the world’s collective security intelligence at your fingertips every time you scan.
Verify Before You Execute
Don’t take chances with your data. Use VirusTotal to verify the integrity of any file or link in seconds.
