Wazuh Review 2025: The Ultimate Open-Source XDR & SIEM Platform

Wazuh Review – The Premier Open-Source XDR & SIEM Platform for Enterprise-Grade Threat Detection (2025-2026)
Wazuh is the world’s most powerful open-source security platform, unifying SIEM and XDR capabilities into a single, high-performance ecosystem. Born as a fork of OSSEC, it has evolved into a comprehensive security suite that monitors endpoints, cloud workloads, and containers in real-time. In 2025, Wazuh stands as the definitive alternative to high-cost proprietary solutions, offering log data analysis, file integrity monitoring (FIM), and automated incident response. Whether you are protecting a small startup or a global cloud infrastructure, Wazuh provides the visibility and agility required to detect advanced persistent threats and comply with PCI DSS, HIPAA, and GDPR mandates without licensing fees.
VERIFIED DATA: Wazuh is trusted by thousands of organizations, including Fortune 500 companies and government agencies. In 2025, Wazuh released Version 4.10+, significantly improving its Agentless Monitoring capabilities and integrating Post-Quantum Secure communication channels between managers and agents. It features native integration with the MITRE ATT&CK framework, allowing SOC analysts to map detections directly to known adversary tactics and techniques.
Security Intelligence: 2025 Technical Metrics
Wazuh’s architecture is designed for Scalability and Depth. It combines lightweight endpoint agents with a powerful server-side analysis engine to deliver near-instant threat alerts.
| Capability Metric | Wazuh 2025 Standard | Expert Technical Analysis (2025-2026) |
|---|---|---|
| Threat Detection | Utilizes a massive rule engine (SCA) to detect everything from weak passwords to sophisticated rootkits and CVE exploits. | |
| Response Agility | Active Response Engine | Can automatically trigger scripts to block IPs, isolate infected hosts, or kill malicious processes the moment a rule is triggered. |
| Cloud Visibility | AWS, Azure, GCP & M365 | Native modules for monitoring cloud activity logs (CloudTrail, Activity Logs) and protecting containerized environments like **Kubernetes** and **Docker**. |
| Compliance Auditing | PCI DSS, HIPAA, NIST, GDPR | Built-in dashboards provide “Audit-Ready” status for global compliance frameworks, mapping logs directly to specific regulatory requirements. |
| Endpoint Intelligence | Inventory & Vulnerability | The Wazuh agent performs continuous **Vulnerability Detection** by comparing installed software versions against the global CVE database. |
Deep Dive: Why Wazuh is the Heart of the Modern SOC
In the 2025 digital landscape, the distinction between endpoint security and network monitoring has blurred. Wazuh sits at the intersection, providing a Unified Security View that traditional SIEMs often struggle to achieve without expensive third-party integrations.
1. Unified XDR: Beyond Simple Log Aggregation
Traditional SIEM tools focus on collecting logs. Wazuh, as an Extended Detection and Response (XDR) platform, goes deeper. It doesn’t just record that a file was modified; its File Integrity Monitoring (FIM) module records who modified it, what was changed, and which process was used.
- Behavioral Analysis: Wazuh looks for patterns. If a user suddenly logs in from a new IP and begins modifying system files, the engine correlates these events into a single “Incident” rather than ten fragmented alerts.
- System Inventory: It maintains a real-time list of hardware, software, and network configuration for every endpoint. This is vital for “Shadow IT” detection and ensuring compliance baselines are maintained.
- Malware Detection: By integrating with **VirusTotal** and **YARA**, Wazuh agents can automatically scan newly created files for malicious signatures, providing an additional layer of defense on top of your standard antivirus.
2. The “Active Response” Advantage
Detection is useless without timely action. Wazuh’s Active Response system is what truly sets it apart. It allows you to configure automated scripts that fire when specific alerts reach a certain severity level.
For example, in a 2025 ransomware simulation, a Wazuh agent can detect the rapid encryption of files, trigger an alert, and instantly isolate the host from the network to prevent lateral movement. This reduces the time to respond from hours to milliseconds, potentially saving an organization from a catastrophic data breach.
3. Post-Quantum Readiness & Future-Proofing
The 2025 release of Wazuh has introduced significant architectural updates to handle the looming threat of quantum computing. By updating its Agent-to-Manager communication protocol to support Post-Quantum Cryptography (ML-KEM), Wazuh ensures that the sensitive security telemetry being sent across your network cannot be decrypted by future adversaries. This commitment to security research ensures that Wazuh remains the definitive choice for government and high-security enterprise sectors.
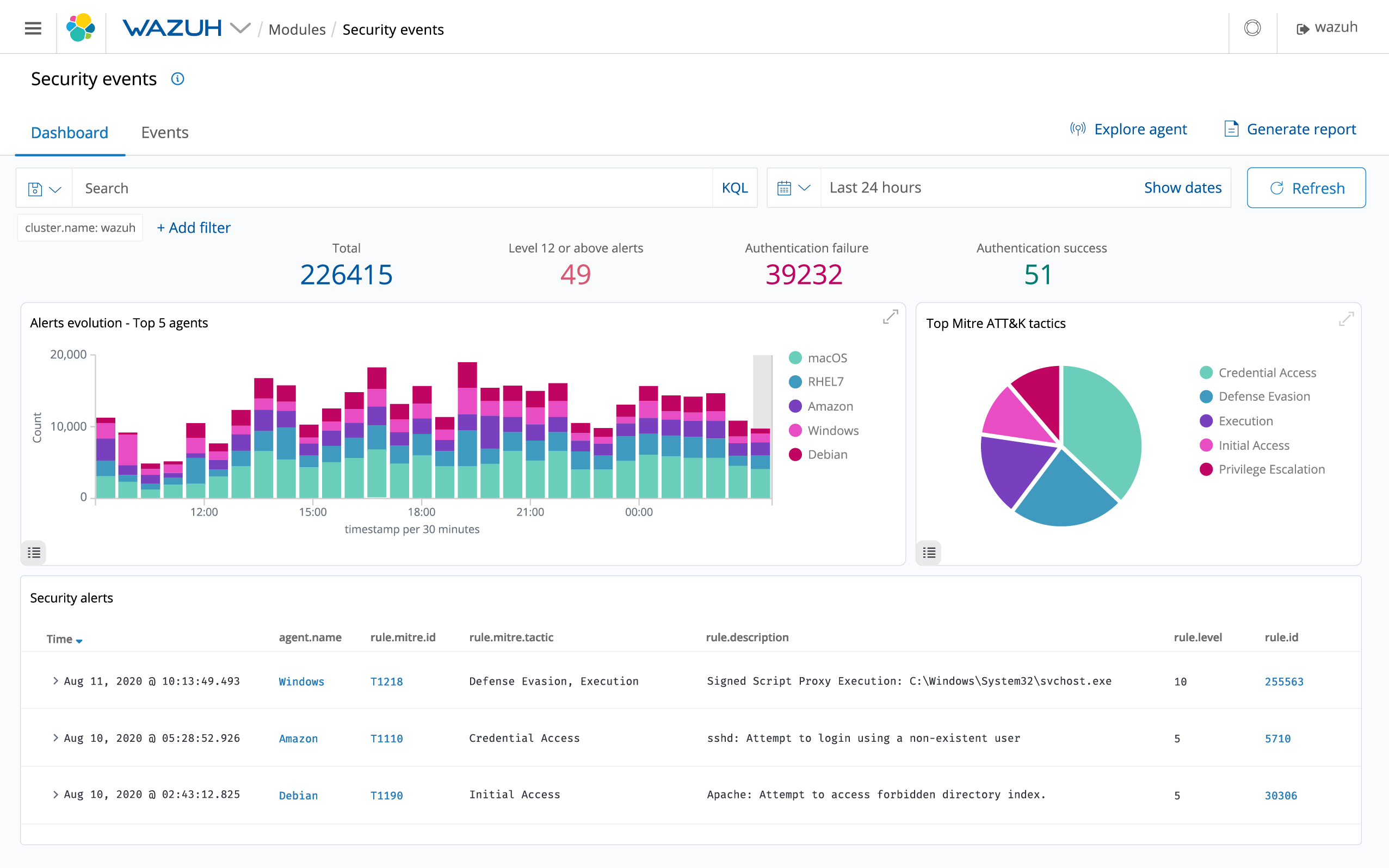
The Wazuh Dashboard: A unified command center providing deep visibility into endpoint health, cloud security, and active threats.
Expert Implementation: Deploying Wazuh at Enterprise Scale
To deploy Wazuh like a professional Security Architect in 2025-2026, follow this Hardened Deployment Strategy:
- Distributed Architecture: For environments with more than 50 agents, always separate the Wazuh Indexer, Wazuh Server, and Wazuh Dashboard into different clusters. This ensures high availability and prevents a single point of failure.
- Leverage SCA (Security Configuration Assessment): Don’t just look for threats. Use SCA to audit your servers against the CIS Benchmarks. This “Hardening First” approach reduces your attack surface before an attacker even arrives.
- Integrate with External Threat Intel: Connect Wazuh to MISP or OpenCTI. This allows your Wazuh manager to automatically flag incoming IPs or file hashes that have been identified as malicious by the global security community.
- Master the Rule Syntax: Don’t rely solely on the 3,000+ default rules. Learn to write custom XML-based rules to detect behavior specific to your custom internal applications.
- Use the API for Automation: Wazuh features a 100% functional REST API. Use it to integrate with your SOAR (Security Orchestration, Automation, and Response) platform or to automate agent deployment via Ansible or Terraform.
Who is Wazuh Best Suited For?
- Managed Service Providers (MSPs): Who need a multi-tenant security platform to monitor hundreds of clients from a single pane of glass.
- Compliance-Heavy Industries: Organizations in Finance or Healthcare that must prove 24/7 monitoring and file integrity for PCI DSS or HIPAA.
- Cloud-Native Startups: Needing a lightweight, agent-based security solution that scales with their Kubernetes or AWS infrastructure.
- Cost-Conscious SOCs: Teams that want the power of Splunk or QRadar without the $100k+ annual licensing fees.
Comparison: Wazuh vs. ELK Stack vs. Splunk
ELK Stack (Elastic)
Primary Strength: Exceptional at log indexing and searching. Weakness: Requires significant “manual labor” to turn it into a security tool; lacks the native security rules and agent intelligence that Wazuh provides out-of-the-box.
Splunk Enterprise
Primary Strength: The ultimate analytical power and massive app ecosystem. Weakness: Extremely high cost; the “Free” version is limited to 500MB/day, whereas Wazuh has no data limits.
CrowdStrike / SentinelOne
Primary Strength: Cutting-edge EDR with professional MDR services. Weakness: Closed-source “Black Box” security; can be prohibitively expensive for mid-sized organizations.
Pros & Cons: The Security Specialist’s Verdict
The Pros
- 100% Free & Open Source: No hidden costs, no data caps, and no user limits.
- Unified Agent: One agent handles FIM, vulnerability detection, and log collection.
- Unrivaled Transparency: Full visibility into the security rules and detection logic.
- Enterprise Scalability: Capable of monitoring 100,000+ endpoints in a distributed cluster.
The Cons
- Management Complexity: Setting up a high-availability cluster requires advanced Linux and networking skills.
- Resource Intensive: The Indexer (OpenSearch-based) requires significant RAM and fast storage (NVMe recommended).
- Steep Learning Curve: Mastering the rule syntax and API integration takes time and dedicated study.
Final Verdict: The Definitve Open-Source Security Backbone
/ 10.0
Wazuh is the single most important tool in the open-source security movement. It successfully bridges the gap between complex log analysis and proactive endpoint defense. In 2025, with its enhanced XDR capabilities and commitment to Post-Quantum security, it has proven that “Open Source” does not mean “Less Professional.” While the initial setup may be daunting for beginners, the reward is a world-class, multi-cloud security platform that you own entirely. If you are serious about building a modern Security Operations Center without being held hostage by proprietary licensing, Wazuh is the foundation upon which you should build.
Protect Your Infrastructure with Wazuh
Stop flying blind. Deploy Wazuh today and get total visibility into your endpoints, cloud, and containers.
